Securing digital twin systems is critical to protecting both virtual models and the physical assets they represent. These systems, which replicate real-world processes using data from sensors and IIoT devices, are increasingly targeted by cyberattacks. A breach can lead to manipulated machinery, data theft, or even physical harm. Here's a quick guide to safeguarding your digital twin systems:
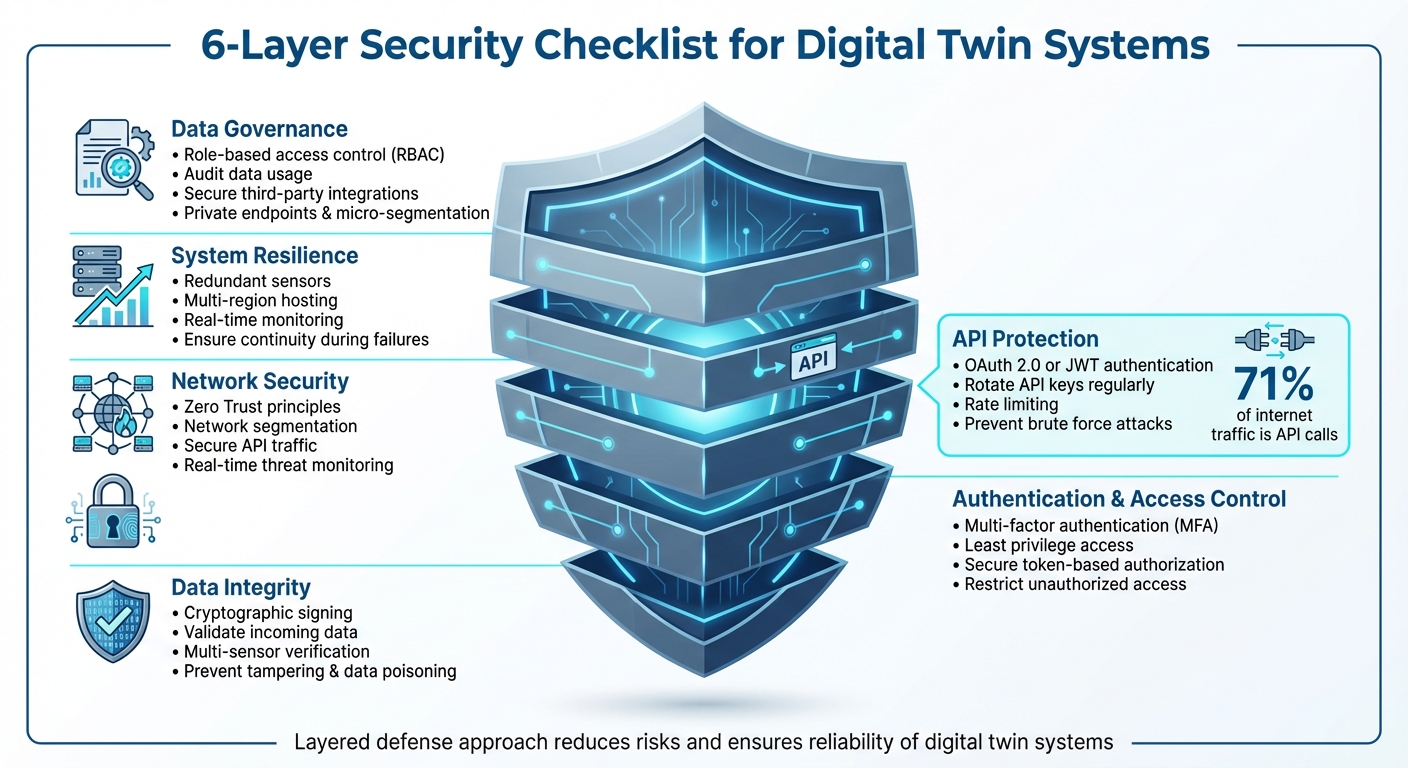
- Data Integrity: Use cryptographic signing, validate incoming data, and employ multi-sensor verification to prevent tampering or data poisoning.
- Authentication & Access Control: Implement multi-factor authentication (MFA), least privilege access, and secure token-based authorization to restrict access.
- Network Security: Adopt Zero Trust principles, segment networks, secure API traffic, and monitor for threats in real time.
- API Protection: Authenticate API calls with OAuth 2.0 or JWT, rotate API keys, and use rate limiting to prevent brute force attacks.
- System Resilience: Deploy redundant sensors, multi-region hosting, and real-time monitoring to ensure operations continue during failures.
- Data Governance: Enforce role-based access control, audit data usage, and secure third-party integrations with private endpoints and micro-segmentation.
These steps create a layered defense, reducing risks and ensuring the reliability of digital twin systems. Cybersecurity isn't optional - it's an ongoing effort to protect both digital and physical environments.
6-Layer Security Checklist for Digital Twin Systems
Cyber-Physical Digital Twins for Intrusion Detection
Security Checklist for Digital Twin Systems
Securing digital twin systems requires a careful, layered approach that addresses potential vulnerabilities across all components - from the sensors collecting data to the networks transmitting it. Below is a checklist to help safeguard your digital twin infrastructure, covering everything from data integrity to network architecture.
Check Data Integrity and Sensor Security
The reliability of a digital twin hinges on the integrity of its data. To protect sensor data:
- Use cryptographic signing and firmware validation: Ensure sensors and IoT devices have secure boot processes that verify firmware cryptographically before it runs. This prevents attackers from injecting malicious code during startup. Employ Hardware Security Modules (HSMs) to safeguard cryptographic keys, even if a device is physically compromised.
- Sign data packets at the message level: While TLS encrypts data in transit, message-level signing verifies the sensor’s identity and ensures the data remains untampered. This is particularly crucial to defend against data poisoning attacks, where altered sensor readings could lead to dangerous physical outcomes.
- Validate incoming data rigorously: Compare data against physical limits and historical trends. Flag anomalies, such as readings that are physically impossible, for immediate review. For critical measurements, use N-version programming by deploying multiple independent sensors to cross-verify data. This ensures that a single compromised data stream won’t lead to a high-stakes error.
"A compromised digital twin doesn't just crash a server; it can cause real-world physical sabotage." - Chris Armour, Director of Software Engineering, Grab The Axe
- Enable graceful degradation: If data reliability is in question, switch to predictive models or require human intervention. For critical decisions, implement a human-in-the-loop system where qualified operators must approve actions before they’re executed.
In addition to securing data, robust authentication practices are essential for protecting your digital twin system.
Set Up Authentication and Access Controls
Securing user and application access is just as important as verifying data integrity:
- Implement a two-step authentication process: First, verify the identity of users, groups, or applications to issue an OAuth 2.0 token. Then, use that token to authorize access to specific digital twin resources.
- Require multi-factor authentication (MFA): MFA adds an extra layer of security, requiring at least two verification steps to reduce the risk of unauthorized access.
- Enforce least privilege access: Grant users only the minimum level of access necessary for their roles. Use managed identities - whether system-assigned or user-assigned - so your digital twin can securely access protected resources like Key Vaults without embedding sensitive keys in code. When assigning roles programmatically, reference roles by their unique IDs to ensure stability across updates.
- Restrict access based on function: For example, some users may only need permission to upload models, while others may require query access or full CRUD (Create, Read, Update, Delete) capabilities. Secure IoT devices feeding data into your digital twin by changing default passwords and disabling unnecessary services.
Use Network Segmentation and Zero Trust Architecture
To minimize the risk of breaches and limit attacker movement, adopt strategies like network segmentation and Zero Trust principles:
- Adopt a Zero Trust approach: Eliminate implicit trust by requiring authentication for every user and validation for every access request. As Anand Oswal of Palo Alto Networks explains:
"The concept of Zero Trust is all about eliminating implied trust. Every user needs to be authenticated, every access request needs to be validated, and all activities continuously monitored."
- Segment your network: Isolate different parts of your network to contain breaches. For example, separating Information Technology (IT) networks from Operational Technology (OT) networks reduces the attack surface and limits cross-system contamination risks.
- Secure API traffic with private network endpoints: Use private endpoints to keep API communications secure. Leverage service tags (like "AzureDigitalTwins") in your network security groups to define access rules based on service-specific IP address prefixes that are automatically updated by the provider.
- Identify and protect critical assets: Start your Zero Trust implementation by identifying your "crown jewels" - the most critical IT and OT assets within your digital twin ecosystem.
- Monitor continuously for threats: Deploy tools that provide real-time security inspection, capable of detecting both known threats and zero-day exploits without disrupting operations.
API Security and Threat Intelligence Integration
Ensuring the security of APIs is a cornerstone of protecting digital twin environments, especially when combined with strong data integrity and network segmentation practices. APIs serve as the connectors between various components of a digital twin, but they also represent attractive targets for cyberattacks. Consider this: API calls account for a staggering 71% of all internet traffic, and 40% of organizations reported experiencing an API security incident in the past year. Charlie Klein, Director of Product Marketing at Jit, puts it bluntly:
"It only takes one vulnerable API to poison your entire stack."
The risks are real and costly. In 2023, T-Mobile faced a breach that exposed 37 million customer records due to an unprotected API endpoint lacking proper authorization and token validation. Similarly, in 2020, attackers exploited Zoom’s unprotected /login API endpoint, compromising 500,000 passwords through brute force attacks. These examples highlight the critical need for robust API security and the integration of threat intelligence in digital twin deployments. Below, we’ll explore practical strategies for securing APIs and leveraging real-time threat detection.
Protect APIs with Authentication
Effective API security starts with proper authentication mechanisms. Implement OAuth 2.0 or JSON Web Tokens (JWT) to authenticate users and validate token claims, such as "aud" (audience) and "iss" (issuer), before granting access. Alice Isla Bennett, Security Architect at Aptori, emphasizes the importance of handling API keys carefully:
"API keys are like passwords for systems. If they're mishandled or exposed, they can provide attackers with access to your API."
To further protect sensitive keys, rotate high-risk API keys monthly and lower-risk ones quarterly. For service-to-service communication, use Mutual TLS (mTLS) to ensure that only clients with valid certificates can make requests. Managed identities, such as Microsoft Entra ID, offer a safer alternative by allowing digital twins to access protected resources without embedding secrets in the code. Additionally, enforce the Principle of Least Privilege through Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC) to ensure users and services have only the permissions they need.
To defend against brute force and Denial of Service (DoS) attacks, apply rate limiting to sensitive endpoints like login or password reset pages. Use exponential backoff to slow down repeated unauthorized attempts. Monitor API activity in real time to detect unusual patterns, such as spikes in request volumes, geographic anomalies, or increased error rates (e.g., 401 Unauthorized or 403 Forbidden responses), and block malicious behavior as it emerges.
Integrate Threat Intelligence for Real-Time Protection
Adding threat intelligence to your security stack enhances your ability to identify and respond to emerging risks. By integrating threat intelligence feeds with your digital twin APIs, you can proactively monitor traffic from known malicious sources, such as Tor exit nodes or cloud providers linked to bot activity. Adaptive rate limiting based on IP reputation can further reduce risks. AI can also play a role by identifying deviations from normal system behavior, comparing current activity against established baselines.
When using third-party threat intelligence tools, prioritize secure integration. Employ private access endpoints, such as Azure Private Link, to avoid exposing APIs to the public internet and reduce the risk of data exfiltration. Use strict schema validation (e.g., OpenAPI/Swagger) to ensure that only expected data formats are processed, and limit the amount of information shared with external tools to minimize the potential impact of a breach. To prevent attackers from gaining insights into your system, simplify error messages in API responses. Provide generic 400/500-level responses to users while logging detailed information internally with a correlation ID for debugging and tracking purposes.
sbb-itb-ac6e058
Build System Redundancy and Resilience
Even the most secure digital twin can encounter disruptions. That’s where redundancy and resilience come into play - they ensure your operations keep running smoothly, even when sensors fail, networks falter, or entire regions face outages. Bill Reid, Security Advisor at Google Cloud, describes digital twins as:
"Digital twins are essentially IT stunt doubles, cloud-based replicas of physical systems that use real-time data to create a safe environment for security and resilience testing."
This setup allows you to test failure scenarios without risking production environments. It’s a critical capability, especially as manufacturing companies have seen a 71% increase in threat actor activity between 2024 and early 2025. Building resilience into your system ensures it can handle sensor failures and connectivity issues effectively.
Deploy Redundant Sensors and Multi-Region Hosting
The first step is identifying weak points in your sensor network. Use your digital twin to assess the impact of potential failures - determine how many components would be affected and whether your system can maintain basic operational functionality in a degraded state. Modular designs can help ensure that if one sensor or subsystem fails, the rest of the system continues operating.
To safeguard against regional disruptions, deploy your digital twin across multiple availability zones and regions. Tools like AWS CDK or CloudFormation make it easier to create and manage redundant infrastructure quickly. Managed services with automatic scaling - such as Amazon S3 or AWS IoT SiteWise - can handle sudden traffic spikes without requiring manual intervention. Real-time synchronization between physical assets and their digital twins ensures consistent and accurate data flow.
Platforms like Anvil Labs (https://anvil.so) can simplify the implementation of these redundancy and resilience strategies.
Conduct Regular Audits and Monitoring
Once you’ve established hardware and infrastructure redundancy, continuous monitoring becomes essential. Use your digital twin as a testing ground for failure simulations, evaluating recovery times, manual switchover efficiency, and bottlenecks in your processes. Track metrics like the percentage of critical services that remain operational during simulated internet outages or how well manual operations hold up when sensors go offline.
AI-driven anomaly detection can help spot unusual patterns in system behavior or data flows that may indicate security risks or operational issues. Integrate digital twin logs and alerts into Security Information and Event Management (SIEM) systems for a unified view of your IT and operational technology health. Automated tools like Amazon CloudWatch can send alerts about performance bottlenecks or data throttling, giving you a heads-up on potential system failures. For added security and transparency, consider using blockchain to maintain an unchangeable audit trail of digital twin access and simulation changes, ensuring the reliability of your resilience testing data.
Data Governance and Auditing
Once security measures are in place, the next step is ensuring ongoing compliance and maintaining operational integrity through data governance and auditing. These practices are essential for keeping your digital twin secure and aligned with standards like ISO 27000. They define who can access data, when they can access it, and how it should be used. Without a solid governance framework, risks like unauthorized access or compliance violations can easily go unnoticed.
Start by setting a security baseline that aligns with industry frameworks. Regularly evaluate your digital twin operations against this baseline to identify and resolve configuration drift early on. Classify all workload data based on its sensitivity. This allows you to focus your monitoring and auditing efforts on the areas that are most critical to your organization's needs and regulatory requirements.
Real-world incidents highlight the dangers of weak governance, but implementing strong data governance measures can mitigate these risks. Below, we’ll explore how to monitor data usage effectively and secure third-party integrations to strengthen your digital twin's overall security.
Track and Audit Data Usage
Transparency and accountability start with detailed logging. Use granular role-based access control (RBAC) to enforce the principle of least privilege and create an auditable trail of all access activities. For instance, Azure Digital Twins provides predefined roles like "Data Owner" (full access, role ID: bcd981a7-7f74-457b-83e1-cceb9e632ffe) and "Data Reader" (read-only access, role ID: d57506d4-4c8d-48b1-8587-93c323f6a5a3).
Limit permissions as much as possible, narrowing access to specific digital twin components, such as individual relationships or event routes, instead of granting access to the entire instance. When automating security configurations, rely on role IDs rather than names, as IDs remain consistent across service updates, ensuring your compliance automation doesn’t break.
Integrating your digital twin system with centralized monitoring tools like Amazon CloudWatch or Azure Monitor is another key step. These tools help you track incoming data, visualize logs, and set up alerts for unauthorized access attempts or potential security issues.
Secure Third-Party Integrations
Third-party integrations can introduce risks, so it's vital to adopt a Zero Trust architecture - where no external user or device is trusted by default. Every access request must undergo continuous verification. Use private access endpoints to connect to REST APIs securely over a virtual network, which eliminates public internet exposure and reduces the risk of data leaks.
Before sharing data with external platforms, validate and sanitize exports to protect sensitive information and intellectual property. Employ service tags (e.g., "AzureDigitalTwins") in network security groups to automatically manage IP address prefixes for authorized third-party services. Update these ranges regularly - weekly updates are a good practice - to ensure precise access control.
Network micro-segmentation is another effective strategy. By isolating third-party traffic into separate zones, you can prevent attackers from moving laterally if a vendor connection is compromised. For resources behind firewalls, enable "trusted service" settings and use managed identities to securely route data without exposing resources to the public internet. Tools like Anvil Labs (https://anvil.so) can facilitate secure data sharing and integrations while maintaining strict access controls.
For multi-stakeholder environments, consider leveraging blockchain technology. Distributed ledgers provide a shared audit trail, ensuring data integrity and traceability across all parties involved. Additionally, smart contracts can automate security rules when state changes occur, adding an extra layer of governance.
Conclusion
Protecting digital twin systems is not just about safeguarding virtual models; it's also about securing the physical assets they mirror. With cyberattacks becoming more frequent and sophisticated, the risks are immense. A single breach could lead to the theft of valuable intellectual property or, even worse, the manipulation of physical equipment, potentially endangering lives.
This checklist - covering everything from fortified sensors and Zero Trust architecture to integrated threat intelligence and secure third-party connections - helps address these vulnerabilities step by step.
"Digital twins are only as secure as the measures we put in place." - Akhil Mittal, Security Leader, Synopsys
To make these security measures work, a strong infrastructure is non-negotiable. Platforms like Anvil Labs champion this approach by offering tools for secure data governance, encrypted transmissions, and automated audit trails. Their features, such as cross-device accessibility and secure sharing with access controls, ensure your digital twin data remains protected throughout its lifecycle.
FAQs
How can I protect the accuracy and reliability of digital twin data?
Maintaining the integrity of your data is essential for ensuring that your digital twin system delivers accurate and reliable insights. When data becomes inconsistent or compromised, the ripple effects can lead to poor decisions - like scheduling maintenance at the wrong time or creating unsafe operational forecasts.
To keep your data secure and trustworthy, here are some effective strategies:
- Encrypt your data both when it's stored and while it's being transmitted to block unauthorized access or changes.
- Validate data in real time using automated tools like range checks or anomaly detection to catch inconsistencies immediately.
- Apply cryptographic hashes to confirm data consistency and quickly spot any tampering.
- Keep immutable logs that record data access and modifications with precise timestamps for accountability.
- Perform regular audits to ensure your data aligns with actual conditions and remains reliable.
By adopting these practices - and using platforms like Anvil Labs, which provide secure data storage and validation solutions - you can ensure your digital twin remains a dependable tool for informed decision-making.
What are the essential steps to implement a Zero Trust architecture?
To set up a Zero Trust architecture, the first step is to identify and catalog every asset within your system. Once you have a clear inventory, establish distinct trust zones and policies to segment and secure various parts of your network. Implement least-privilege access, granting users only the permissions they need based on their identity and the specific session. Incorporate micro-segmentation to restrict lateral movement across the network, and ensure all communications are encrypted to protect sensitive data.
Finally, maintain a system of continuous monitoring and validation to spot and respond to potential threats as they arise in real time. These steps work together to strengthen your network's defenses and minimize vulnerabilities.
What are the best practices for securing APIs in a digital twin system?
To keep APIs in your digital twin system secure, it's crucial to use a defense-in-depth approach. Start by ensuring all data in transit is protected with encrypted transport protocols like HTTPS and TLS. Use strong authentication methods such as OAuth 2.0 and JSON Web Tokens (JWT), and always validate tokens against trusted key sets to verify their legitimacy. An API gateway is key for managing traffic, enforcing least-privilege access, and applying Zero-Trust principles, which require every request to be verified, no matter where it originates.
Other essential steps include rate-limiting and throttling API requests to prevent misuse and sanitizing all inputs and outputs to guard against injection attacks. Keep a close eye on activity with continuous monitoring, logging, and automated anomaly detection so you can quickly identify and address potential threats. Regular patching and integrating threat intelligence are also necessary to tackle vulnerabilities as they arise.
Anvil Labs makes it easier to implement these security measures with tools designed for secure data sharing, customizable API endpoints, and enterprise-grade gateways. Their features - like OAuth, JWT support, and detailed audit logs - help ensure your digital twin data remains protected while staying accessible to those with proper authorization.

